I am excited to play a small part in helping to further threat-informed defense by creating an opportunity for individuals to more efficiently, effectively, and accurately learn the principles, strategies, and methods for creating a proactive cyber defense.
There are a lot of terms and concepts in the cybersecurity industry (EDR, SIEM, Zero Trust, MFA, APT, etc.) and Threat-Informed Defense is no exception to the list. However, unlike the acronyms, it is not easy to comprehend the term with a simple Google search. To best understand Threat-Informed Defense, a mix of frameworks, strategies, and goals should be combined with practice and testing. I want to help quicker the learning process and time it takes people to learn what Threat-Informed Defense is and why it should be a focal point of defenders.
What?
A single website where people can learn the ins and outs of threat-informed defense (TID) from the top voices, practitioners, and organizations in the industry. From threat intelligence to adversary emulation and threat modeling, the field of TID continues to grow and mold into something that will become the norm of cybersecurity strategy for years to come.
Specifically, the Threat-Informed Defense Ecosystem is a start.me page full of links to resources, products, strategies, educational tips, and guides for applying a threat-informed cyber defense strategy. However, instead of just bulk listing materials in the name of “helping,” I wanted to go further and actually educate. I've seen too many "top 10 lists," brain dumps, and GitHub sites to know that just sharing resources is not a very beneficial training method. Some people can learn exceptionally well on their own, but most people need context and direction to properly comprehend information.
To accomplish this structured learning, I categorized and labeled resources into useful sections such as the major pillars of TID, the various frameworks and models, free training courses and platforms, and the top organizations involved in developing threat-informed defenses. I also added a recommended progression path through this page for those individuals that are completely new to TID and looking for where to start and in what order to learn topics, as many do build upon each other.
Why?
When I first heard about “threat-informed defense,” I couldn’t wait to learn more. An active cyber defense strategy that works to know the enemy and creates defenses to stop their specific tactics? Sounded much better than the current cyber strategies out there. I mean who wants to continually lose the cyber battle because we have no idea what/who we are defending against? As a competitor, I want to win. Anything that gives me a better chance to win is something I definitely want to know more about. So, I searched the internet high and far, but after a few days I was only able to come up with a few articles and talks to learn from (big shout out to MITRE and the ATT&CK team). That was about 2 years ago, and I am thrilled that there are so many more guides, resources, and courses available today. Since I took that initial deep dive, TID has continued to expand and has grown into an entire industry.
This is why I created the Threat-Informed Defense Ecosystem start.me page. I want to help develop practitioners that understand how to apply practices and techniques of TID. My goal is to provide everything one needs to become a TID specialist, from 0 to 90ish, without an overwhelming amount of resources/lists/links. The largest issue with self-learning today is that so much information is available, but there is not much vetting as to the accuracy of that information. Anyone can post something, but is that information actually something worth listening to?
My subpar experience of learning how to create a threat-informed defense led me to seek a way to make it easier for others to learn. I was confident that there had to be an easier way than spending hours on the internet and only finding 5 or 6 useful items.
Well, I did the hard work and gathered the most critical knowledge pieces in one place so that you don’t have to.
For?
YOU!!!
Well really, anyone that is currently working in cybersecurity or would like to one day.
I firmly believe that everyone helping to protect an organization or nation in cyberspace should fully understand the terms and principles applicable to TID. A threat-informed mindset is something that can assist both the smallest businesses and the largest countries. Small businesses will look to justify spending and make the most of the controls they have implemented, while nations seek the protection of their critical data and knowledge of adversaries looking to steal it. Both are highly influenced by threat-informed defense actions.
Content
Within the Threat-Informed Defense Ecosystem, you will find a variety of categories of information. Each section is filled with the information you should know regarding that specific topic. This includes learning objectives and links organized by resource type (pdf, article, blog, video, etc.).
The topics that have been added so far (as of April 2023) are:
Introductory Readings
The background, beginnings, and definition of threat-informed defense.
Frameworks and Models
A review of the frameworks and models that make up TID. Included in this section is MITRE ATT&CK and D3FEND, and the Cyber Kill Chain, Unified Kill Chain, Diamond Model, and the Pyramid of Pain.
MITRE ATT&CK Study Guide
A deep dive into resources, use cases, and strategies for using ATT&CK to improve cyber defenses.
Center for Threat-Informed Defense
An understanding of the mission of CTID and a list of every project CTID has published with partners to help further TID practices.
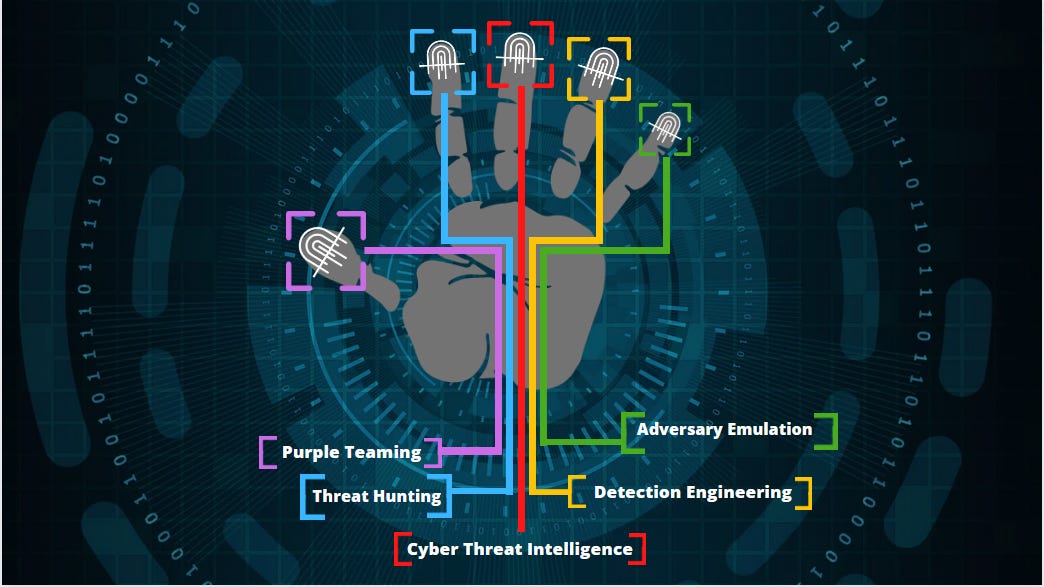
The Pillars of TID (6)
Intros to cyber threat intelligence, threat hunting, threat modeling, purple teaming, adversary emulation, and detection engineering. Each pillar gives info that will help viewers understand the what, why, and how for each topic.
Free Training Courses and Testing Labs
A list of free training courses and labs that can be used for hands-on practice.
Free and Paid TID Platforms
Some of the top platforms designed to assist with implementing TID.
Leading TID Organizations
Listing of the top organizations in the TID space that offer products, platforms, and services to help other organizations achieve TID.
ATT&CK Evaluations

An explanation and use cases for the ATT&CK evaluations program.
Final Remarks
This page relies heavily on freely available resources and materials. All content and resources are the intellectual property of the applicable creators and may be protected under copyright laws of the United States and/or other countries. I do not claim to own or have created anything that does not have my name on it. All trademarks are the property of their respective owners.
You will see some names show up more than once on here. I'd highly recommend you look further into talks, projects, blogs, and social media from these people. They are some of the trailblazers for threat-informed defense.
I plan to release a separate blog post to further explain and provide more context for each pillar of TID. So you can expect a part 2, 3, 4, 5, and 6 down the road.
Project Link and Contact Info
The Threat-Informed Defense Ecosystem site link is: TID Ecosystem Project
For recommendations, comments, or concerns on this project, I can be reached via LinkedIn at: Micah's LinkedIn