Purple Team Part 1: Starting a Purple Program
Build it and they will.... at some point realize the immense value and hail you the wisest of them all
A few months back I spoke at a local cyber conference on the topic of building a purple team program. The presentation focused on providing practitioners and leaders with multiple methods, metrics, and tools that can be used to improve cyber prevention, detection, and response capabilities within an organization. I firmly believe that by utilizing the threat-informed defense principles of cyber threat intelligence, defensive countermeasures, and testing and evaluation, an organization of any size can start a purple team program that is able to scout, prepare, and react to adversaries in a proactive approach. I wanted the information to be applicable to both mature and newly developed programs/teams, offering suggestions to establish, measure, test, and improve an organization's purple team presence and ability to combat real cyber attacks.
It seemed to receive positive feedback, so I wanted to turn the talk into a two-part blog series that people could read who maybe didn’t get to hear it in-person or just prefer to digest a text format. This first blog will focus on the program side of things, such as why, the benefits, what (staffing, mission), maturity levels, and performance metrics for purple teams. The second blog will look into some of the tools and methodologies to deploy when performing purple team functions involving CTI, BAS/emulation, and detection engineering.
Purple teaming is a challenging function for most organizations to perform well. There are many reasons why this is so, but I suspect that at the top of the list is that small companies lack the skill and time for such an effort, and large companies are often too segmented in security roles/teams for such a holistic program to be effective. There are definitely some fantastic purple team programs out there, but the norm is certainly a lack in this capability department. Considering that a purple team exercise is really composed of roughly 4-5 unique skillsets, it makes sense that only the most mature teams currently work in this level.
Why Purple Team Functions are Needed
Well, for starters, new compromises and breaches are occurring every day, and with the continual increase in making everything internet-connected (because it’s a feature), expanding attack surface, and the disregard for security, this will likely continue for a very long time.
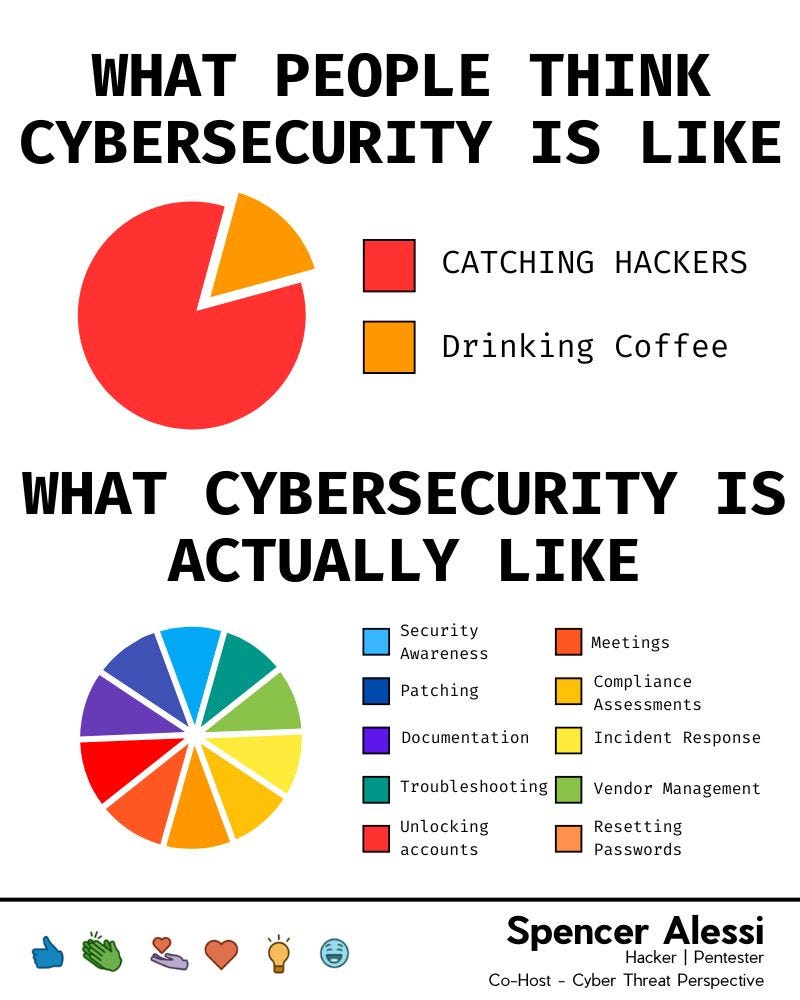
Cybersecurity is hard. There is no denying that. Consider the number of vendors, products, best practices, and frameworks that exist, and you need an expert just to make sense of it all. Now let’s think about the fact that many of the largest cybersecurity companies are heavily involved in incident response… I think that alone should tell us something about the industry. Cyber defense is not a simple man’s game. While there are many reasons why this might be, we usually can’t blame our security team. Their mission might be to protect the company, but they are almost certainly swamped in work that doesn’t always align with that goal. There probably isn’t a better way to explain this than the image created by Spencer Alessi.
Welllll if we can’t do everything, we at least should be able to keep our systems patched, right? Yeah go fish on that one. The Cyentia Institute researched remediation of vulnerabilities, and trends around vulnerability management. Spoiler, they found out it’s basically impossible. In their report “The Fast and the Frivolous” they analyzed the capability of companies to patch their vulns, and it was concluded that 50% of companies can only patch around 10.3% of their vulns in any given month. A fun fact that was thrown in is that most company policies require them to patch all Critical or High vulns within 30 days, which accounts for around 58% of vulnerabilities. Ruh roh Shaggy, that’s a lot more than 10%… Might be time to see if you’re being audited on that one.
While stats like this seem to paint a bleak picture, the benefit of knowing this information is that it’s critical we are realistic of our capabilities, and identify what is the best use of our time based on our resources.
Benefits of Purple Team Exercises
So back to purple teaming, what benefits could an organization gain by having purple team capabilities?
Stop breach impact with robust detection + rapid response
Deny adversaries easy attack vectors
Improve resilience to compromise
Inflict pain of change on adversaries.
Prioritization (patching, controls, time, $)
identify the best ways to spend your critical limited resources
Gap identification
Identify gaps in defense before someone else does
Train operators
The best training happens in your environment, to realistic situations
Cut through FUD
I’ve noticed a trend in cybersecurity, and that is the concern for things that are very unlikely to occur. The worry of APTs, AI hype, and vendor FUD has gotten a lot of companies’ focus misaligned. The resources are put into stopping advanced threats, while they have forgotten the fundamentals.
“When it comes to the HOW of so much adversary activity: focusing on exploiting vulnerable systems (and NOT with "zero days"), targeting users, buying access from infostealer networks, and similar… defenders have gone "all in" on advanced security mechanisms, while adversaries continue to thrive through subversion of security basic best practices.” - Joe Slowik MITRE ATT&CK Lead. Cybersecurity doesn’t have to be as complicated as we make it, but most companies lack a threat model and the ability to cut through the noise and focus on what matters most for them.
What is a Purple Team Program?
Before we get into what it looks like to run a killer purple team program, let’s talk a little about successful programs in general. For anything to be successful, it always comes down to the leadership. Without good leadership, the ship will either float around aimlessly or sink faster than the last cold call you accidentally took. So, we must ensure our program is set up for success, and this takes leadership defining the:
Culture
Mission
Vision
Resources
Let’s make sure we understand these items before moving on.
Culture - Who are we
Purple team example: Multi-team group possessing various cybersecurity and organization-specific skill sets working collectively
It is important here that we seek integration & collaboration, not a siloed purple team that works outside of business workflows and processes.
Mission – What do we do
Purple team example: Utilize continuous collaboration to test people, processes, and technology (controls) against relevant attack methods
It is important here that we test to improve, not to shame or hand slap people.
Vision – Define OUR successful program
Purple team example: Improve organizational cyber defense resilience through gap identification and validated prevention, detection, and response
For your vision, the more specific with it you are, the better the odds of reaching it will be. Think of a GPS, the more specific the information entered, the more likely you are to reach that destination. If you want to get to Cedar Point, and you only entered Ohio into the GPS, you’re going to be driving a good while (and see a lot of corn fields) before you find Cedar Point.
Resources – What is needed to accomplish our mission
Purple team examples:
People (defenders, attackers, CTI, sysadmins, managers)
Visibility - Logs from endpoint/host, network, identity
Intel collection and operationalization
Defensive controls
Testing capability
This one is really all about people, processes, and data (not just technology), people matter! Cyber has a fixation on tools, tech, and shiny new things. However, the MOST important thing to any successful program is the people. Simon Jeffries, an Ex-Special Forces member, wrote that “The secret to Special Forces is intensive, ceaseless, meticulous training and preparation. The quality of your operators matters far more than the equipment.” The same is absolutely true when it comes to cybersecurity. Enjoy this meme
Skills, training, and preparation are key. People and processes will win out over time. The right people can do a lot more than tools with no one to use them (yes I am an AI doubter).
So after all of that, what is a Purple Team Program?
My definition would be: The collaboration of relevant multi-team members and skills working together that continuously test people, processes, and technology controls against relevant attack methods to improve organizational cyber defense resilience through gap identification and validated protection, detection, and response. This function is accomplished through utilization of people, environment visibility, intel, defensive controls, and a testing capability.
Can you spot the culture, mission, vision, and resources in the statement above?
Poor Purple Teams
Now it can also be useful to identify what a purple team is not. Please don’t let this be you:
A siloed group that functions alone
Doesn’t track metrics
Doesn’t provide actionable recommendations
Just does vulnerability assessments
Requires an internal red / CTI teams
Requires elite expertise of every cybersecurity domain
There is nothing inherently wrong with the last two bullet points, however some people can get caught up in what they need, and then believe the goal is unattainable if they do not have those things. You do not need an internal red team and CTI team to do purple team exercises. And you definitely don’t need to be a unicorn (but you should check out Scythe who puts out a look of purple team resources).
Maturity Levels of Purple Teams
One very important part of progress is having direction, or simply identifying what the next level looks like. To get anywhere, you must first know where you are and then decide where you want to be. I see there being four levels of maturity for Purple Teams.
One Time Engagement
Give it a try one time
Ad-Hoc Exercises
Can perform this capability, but it takes time to spin up and utilize
Requires moving people or resources from other workflows to accommodate
Varied success rates
Regular Exercises
Regularly meets the need based on the current volume of having to deploy this capability
Success rate is a reasonable level
Not viewed as a strain on operations to deploy this capability
Continuous Purple Teaming
Operationalized effort, performs capability quite often or with near 100% success rates
Someone or something (tech) is designed to operate this workflow as a primary responsibility
The environment is set up so that using this capability is second nature
A good chunk of the definitions for levels 2 through 4 can be attributed to Max Rogers, Sr Director SOC at Huntress. Great job identifying high performing teams Max! Scythe labeled the Continuous Purple Team level as an Operationalized Purple Team in their Purple Team Exercise Framework. The below graphic gives a great overview of the workflow of this capability in action.
Other Maturity Models / Frameworks
I wanted to provide resources for a few other maturity models and frameworks that could be used to grow specific aspects of the purple team. From general threat-informed defense to CTI, hunting, and detection engineering, there’s a lot of work that can be done in each section. These are some amazing pieces of work that could each have their own dedicated blog.
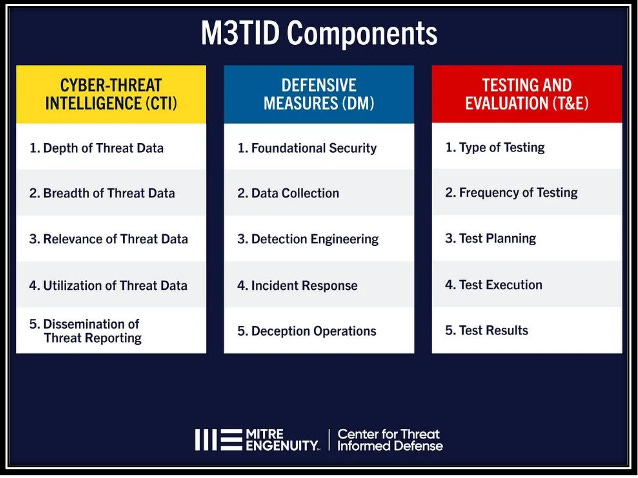
MITRE CTID - Measure, Maximize, and Mature Threat-Informed Defense (M3TID)
Cyber Threat Intelligence Capability Maturity Model (CTI-CMM)
Mandiant - CTI Program Maturity Assessment
SCYTHE - Purple Team Maturity Model (PTMM)
Kyle Baily – DE Maturity Matrix
Sqrrl - Hunt Maturity Model
If you think the Sqrrl model is outdated, you can look into the Splunk PEAK framework for threat hunting. It doesn’t give progression levels, however, it’s focus is more on the methodology of threat hunting.
I have included the above items plus a lot more in the Threat-Informed Defense Ecosystem project if you would like to learn more on the topics of purple teaming, CTI, detection engineering, threat hunting, adversary emulation, and threat modeling.
Metrics to Measure Effectiveness / ROI
Alright, we’re nearing the end of part 1 of the purple team blog series, but before we finish, we cannot skip out on the most important part of cybersecurity, metrics!
Hopefully you picked up on my sarcasm there. Metrics are usually awful, and just one more thing that takes up our time and stops us from focusing on stopping bad guys. But with that being said, nearly all cyber teams are historically bad at communicating value-add. And because of this, we get left behind teams that can clearly display metrics and prove value to the C-Suite (marketing, product, etc). So we need to make sure we can effectively display the value of having a purple team.
The goal of metrics is to effectively demonstrate the value of the security program and our efforts. But we don’t want just any metrics. We want mature metrics that align with our business objectives.
“Mature metrics are correlated with business goals, outcomes and enablement. You measure on performance & effectiveness.” - Gert-Jan Bruggink
I could tell you what I think you should do or what not to do with metrics, but Gert-Jan already put together some great resources here. Go check those out, for this purpose, specifically go to the CTI and Threat Informed Defense sections. He lays out some great examples and items to consider, such as:
High level status of program
Value to the business (cost savings and control enhancements)
Key change activities (strategic initiatives)
Major threats tracked
Major risks tracked
People controls
Technical controls
Regulatory compliance
Total number of incidents
MTTD: average vs exercise
MTTR: average vs exercise
That’s all for now, part 2 will focus on tools and how to actually run a purple team exercise.